Why Are Salesforce Shield and Zero Trust Important in 2025?
In today’s fast-moving digital world, traditional security approaches are no longer enough. With more businesses moving to cloud platforms like Salesforce, the need for smarter, more adaptive protection strategies has never been greater. Enter Zero Trust, a security framework that takes the stance of “never trust, always verify”, requiring every action, user, and device to be constantly validated. Combined with the growing power of AI-driven tools, the game has changed – allowing businesses to automate threat detection in real time.
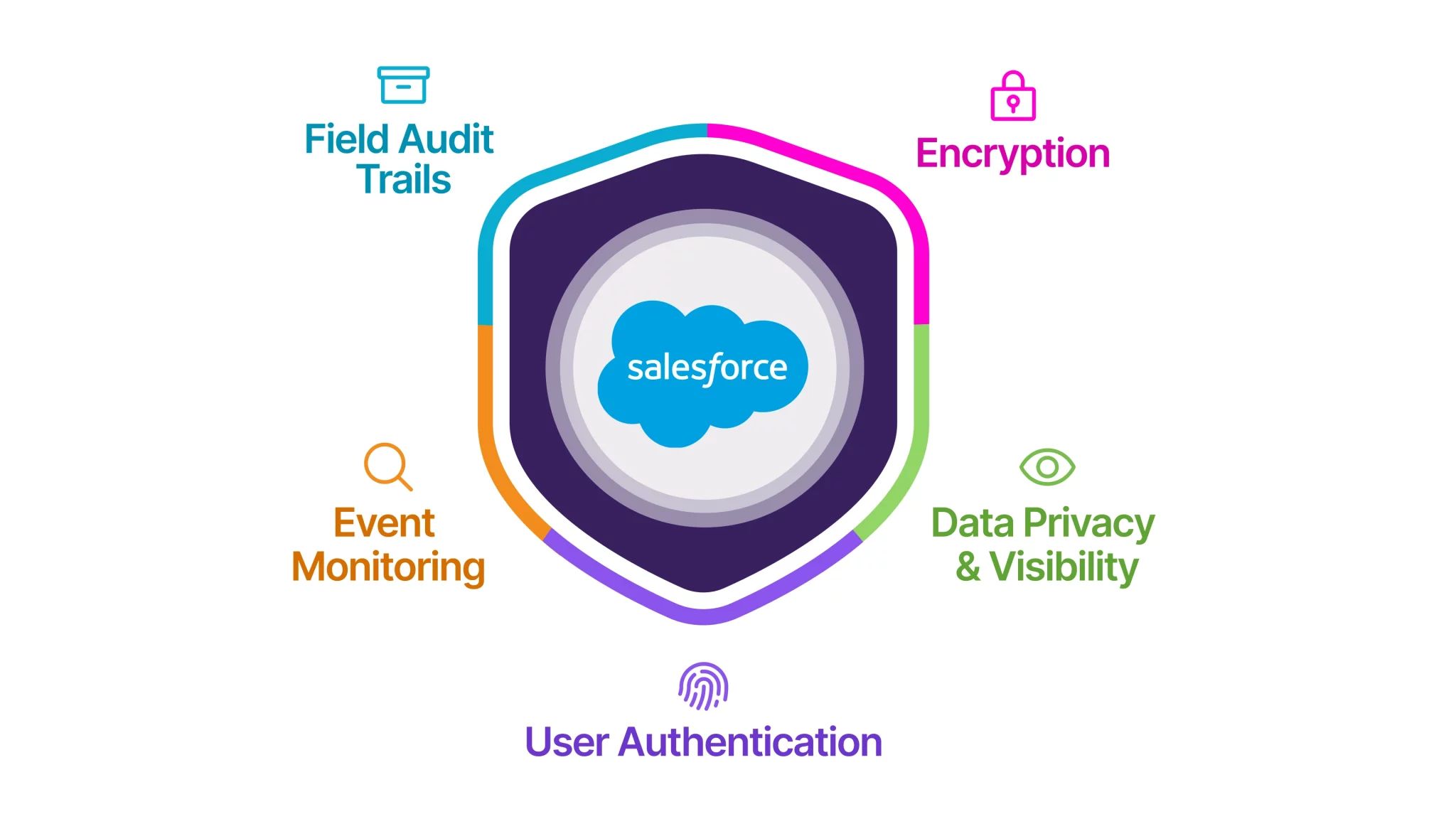
Pairing these technologies with Salesforce Shield creates a powerful combination that not only safeguards your data but also anticipates potential threats before they escalate. In this article, I’ll dive into how Salesforce Shield features like Platform Encryption, Event Monitoring, and Field Audit Trail work hand-in-hand with standard Salesforce security functionalities to build a robust Zero Trust framework in your Salesforce environment.
Aligning Zero Trust with Salesforce’s Core Value of Trust
At its core, Zero Trust challenges the traditional idea of internal security, where anything inside the network is inherently trusted. Instead, it requires that every access request – whether it’s a login, a data query, or a transaction – must be verified at multiple layers. This reduces vulnerabilities and strengthens overall security.
In a Salesforce environment, this approach aligns closely with Salesforce’s core value of Trust. Salesforce has always put trust at the center of its customer relationships, and a Zero Trust framework reinforces that value by making sure security is built into every interaction, not assumed.
It’s no longer about just securing a perimeter; it’s about making sure that every single access point is controlled and validated to keep your data safe and your organization compliant.
Leveraging Salesforce Shield for a Zero Trust Security Approach
Salesforce Shield offers the perfect tools to bring Zero Trust principles to life, delivering multiple layers of security, visibility, and control.
Field Audit Trail: Preserving Data Integrity
Maintaining a detailed record of all data changes is vital in a Zero Trust set up. Field Audit Trail allows you to track modifications to critical data fields, giving you full visibility into who made the changes, when, and from where.
An immutable log of changes means that you can quickly identify unauthorized edits and take steps to revert them. This reinforces the principle of least privilege by ensuring users only have access to modify data relevant to their roles.
Best Practices:
- Enable Field Audit Trail for key fields in regulated industries, like finance or healthcare, where maintaining data integrity is critical for compliance.
- Pair it with Event Monitoring to get a full picture of both data modifications and the actions leading up to those changes.
Imagine working in the financial sector, where changes to critical financial data could have severe legal consequences. Field Audit Trail helps create accountability by showing exactly who made changes and when, preventing costly mistakes or fraud.
Final Thoughts
Incorporating Salesforce Shield into a Zero Trust framework is about more than just preventing threats; it’s about continuously adapting to them.
Features like Platform Encryption, Event Monitoring, and Field Audit Trail don’t just protect your data, they actively help you anticipate and mitigate risks before they escalate. By building a security model where every action is validated and every user is monitored, you reduce the risk of breaches while fostering a deeper sense of trust within your organization.
With Salesforce Shield and Zero Trust working together, you can ensure that your business is prepared for the evolving cybersecurity landscape, making security an integral part of every interaction.
At MagicFuse, we’ve seen firsthand how pairing Salesforce Shield with Zero Trust creates a powerful security boost, giving businesses the edge they need to tackle today’s security challenges with confidence.
Let’s break down each of these features and how they contribute to building a Zero Trust environment.
Platform Encryption: Securing Data at Its Core
Encryption is foundational to Zero Trust, ensuring that even if someone manages to break through your defenses, the data they access remains useless. Platform Encryption in Salesforce Shield helps encrypt sensitive data both at rest and in transit, making sure that critical information such as personal identifiers or financial records remains protected.
Managing your own encryption keys gives you full control over who can decrypt and view sensitive data. Even if an attacker bypasses other layers of defense, the data is still safe.
Best Practices:
- Deterministic encryption works best for fields where you need exact matches, such as social security numbers or account numbers.
- Use probabilistic encryption when you don’t need exact matches, such as for sensitive medical or financial data, where flexibility in filtering is important.
Take the case of healthcare organizations: encryption can ensure that patient data is only accessible by authorized personnel, even within the same system. This level of granular control is critical for both regulatory compliance and protecting patient privacy.
Event Monitoring: Continuous Monitoring and Threat Detection
In a Zero Trust model, monitoring is non-negotiable. Event Monitoring gives you visibility into everything happening in your Salesforce org – from login attempts to data exports, providing the information you need to detect anomalies.
With continuous tracking of user actions, Event Monitoring makes it easy to spot suspicious behavior in real-time. For example, unusual login attempts or large-scale data exports can trigger instant alerts, allowing for swift action.
Best Practices:
- Set up transaction security policies to flag or block risky actions, like massive data downloads.
- Regularly review login history to catch potential breaches, such as repeated failed logins from unknown IP addresses.
- Integrate Event Monitoring with third-party security systems for more holistic threat detection.
Think about a scenario where a sales rep is suddenly exporting massive amounts of customer data at odd hours. This could be a red flag for insider threats or compromised credentials. With Event Monitoring, you can catch this activity early and prevent serious data breaches.










